With US government agencies and lawmakers reportedly considering banning TP-Link products in the US, one would think the company would be high on the list of network providers with the most vulnerabilities currently being exploited by cyberattackers.
Not by far.
The Chinese company, whose products are popular with consumers and small businesses, currently has two security issues on the Cybersecurity and Infrastructure Security Agency’s (CISA) List of Known Exploited Vulnerabilities (KEV), compared to 74 for Cisco Systems and 23 for Ivanti. , and 20 for D-Link.
Yet U.S. government officials worry less about known vulnerabilities than about unknown risks, including the popularity of their routers in the United States — where they account for about two-thirds of the market — and the extent to which the company is owed The Chinese government.
Although no researchers have reported a specific backdoor or zero-day vulnerability in TP-Link routers, restricting products from a political and economic rival country is not unreasonable, says Thomas Pace, CEO of the Expanded Internet of Things (IoT) security. NetRise company and former cybersecurity official for the U.S. Department of Energy.
“To me, the value (of a ban) is almost more about economic policy than the pure technical value of cybersecurity,” he says. “To me, it’s helpful to say that you shouldn’t buy these things for reasons X, Y, and Z (and to make) it harder for small businesses, or anyone, to get their hands on the devices of these companies.
TP-Link – Not a vulnerability that stands out
As of April 2024, one of two TP-Link vulnerabilities has attracted the most vulnerability scans by malicious actors, according to an analysis by cloud and application security company F5. The problem, a command injection vulnerability for TP-Link’s Archer AX21 router (CVE-2023-1389), allows an unauthenticated attacker to easily compromise a device via a simple POST request.
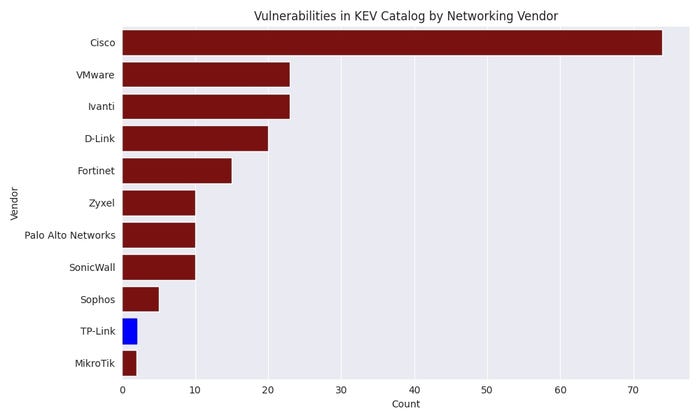
TP-Link ranks low on the list of network providers with known exploited vulnerabilities. Source: Author based on CISA data
In another incident, security firm Check Point Software Technologies discovered that TP-Link devices were also compromised by an implant known as Camaro-Dragon. The implanted components were discovered in modified TP-Link firmware images, not in the original software shipped by the company, says Itay Cohen, head of research at Check Point Research.
Still, Cohen emphasizes that the implants were written in a firmware-independent manner and not specific to any particular product or vendor.
“It should be noted that this type of attack does not specifically target sensitive networks, but rather traditional residential and home networks,” he says. “Therefore, infecting a home router does not necessarily mean that the owner was a specific target, but rather that their device was just a simple means an end for the attackers“.
The threat posed by these vulnerabilities and implants is real, but KEV catalog data shows that other manufacturers are just as likely to have their vulnerabilities exploited – and there are more of them. The lesson is that vulnerabilities in embedded devices are not unique to a manufacturer or country of origin, says Sonu Shankar, product director at Phosphorus Cybersecurity, a broad IoT cybersecurity provider.
“State actors frequently exploit weaknesses in devices from companies around the world, including those sold by U.S. manufacturers,” he says. “Devices lacking basic security hygiene, such as using strong passwords, applying timely firmware patches, or proper configuration, can become easy targets for cyberattacks.”
TP-Link highlighted this fact in a statement sent to Dark Reading.
“Many consumer electronics brands are being targeted by hackers and we support the government’s efforts to hold all producers to the same standards,” a company spokesperson said. “We are open to opportunities to collaborate with the federal government to demonstrate that our security practices are fully compliant with industry security standards and to demonstrate our continued commitment to the American market, American consumers and responding to risks for national security of the United States.”
Chinese government surveillance is pervasive
But these claims perhaps downplay the Chinese government’s influence over the company’s operations: Most Western companies don’t understand the extent to which Chinese authorities monitor Chinese industries – and cybersecurity companies – in part of government policy and national strategy, according to Pace of NetRise. said.
“It’s a totally different company culture,” he says. “There’s a PRC member in every company. It’s not even an opinion, it is what it is. And if you think they’re not there to exert influence, then you’re just an incredibly naive person, because that’s exactly what they do, (including) for intelligence gathering purposes.”
Threat intelligence analysts have pointed to the Chinese government’s national strategy documents and evidence showing its growing efforts to compromise rival countries’ infrastructure – such as attacks by Typhoon Volt and Typhoon Sel.
“In recent years, we have seen growing interest from Chinese threat actors in compromising edge devices, with the aim of both building resilient and more anonymized C2 infrastructure, and gaining a foothold in certain targeted networks,” Check Point said in its analysis, but added that the “discovery of the firmware-independent nature of implanted components indicates that a wide range of devices and vendors may be at risk.”
Chinese networking products aren’t the only ones being targeted by the US government, which bans products from antivirus company Kaspersky for national security reasons, given that it is a Russian company.
The Global Cyber Reality of Home Routers: Buyer Beware
Businesses and consumers should do their due diligence, keep their devices up to date with the latest security patches, and determine whether the manufacturer of their critical hardware may have secondary motivations, says Phosphorus Cybersecurity’s Shankar.
“The vast majority of successful IoT attacks are enabled by preventable issues such as static, unchanged default passwords or unpatched firmware, leaving systems exposed,” he explains. “For commercial operators and end users, the bottom line is clear: adopting basic security hygiene is a critical defense against opportunistic and sophisticated attacks. Don’t leave the front door open.”
For businesses concerned about the origin of their network devices or the security of their supply chain, finding a trusted third party to manage the devices is a reasonable option. In reality, though, almost all devices should be monitored and untrusted, says NetRise’s Pace.
“There’s a crazy world out there when it comes to device security,” he says. “You accept this device that you know nothing about – and really can’t know anything about – unlike Windows (or another operating system)… where you can also put three agents and a firewall in front of it to mitigate software risk.


